Whitelist localhost? - The Security Theater of OAuth Redirect URIs with MCP
Why some MCP providers are building metal bars for windows while leaving the back door wide open
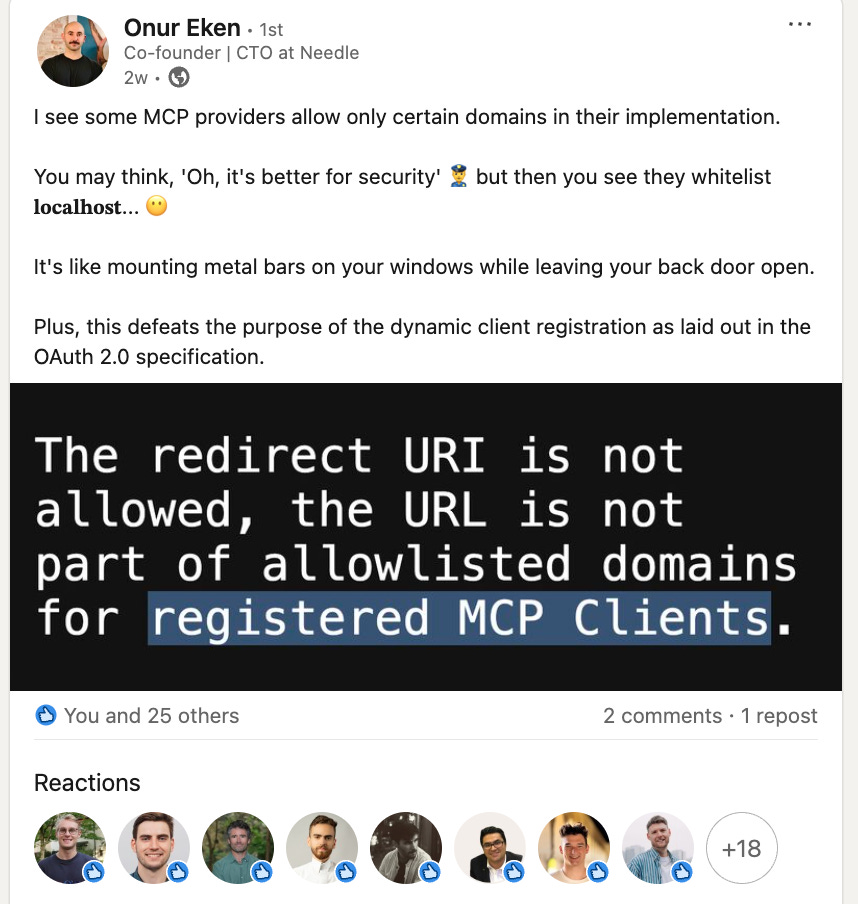
We've been observing something peculiar in the OAuth implementation landscape lately. Some MCP (Model Context Protocol) providers have adopted a seemingly security-conscious approach: they only allow certain domains in their OAuth redirect URI configurations.
At first glance, this sounds reasonable. "Oh, it's better for security!" 🤔
But then you dig deeper and discover they whitelist localhost... 🤦♂️
The Localhost Paradox
Here's what makes this approach so counterproductive: localhost is literally the least secure environment you could whitelist.
Think about it:
Any malicious application running on a user's machine can spin up a local server
No certificate validation occurs with localhost
Local network attacks become trivial
There's zero accountability or audit trail
Meanwhile, legitimate production applications with proper HTTPS, certificate validation, and security monitoring get blocked because their domain isn't on some arbitrary allowlist.
It's Like Installing High-Tech Security Cameras on Your Front Door While Leaving Your Back Door Wide Open
You're meticulously securing one entry point while creating a massive vulnerability elsewhere. It's security theater at its finest – looking secure while actually making things less secure.
Breaking OAuth 2.0's Core Design
This approach fundamentally defeats the purpose of dynamic client registration as outlined in the OAuth 2.0 specification. When you restrict redirect URIs to a predetermined allowlist, you're essentially saying "we support OAuth 2.0, except for the parts that make it useful in real-world scenarios."
What Actually Improves OAuth Security:
Instead of arbitrary domain restrictions, focus on measures that address real attack vectors:
✅ PKCE (Proof Key for Code Exchange) - Prevents authorization code interception
✅ State Parameter Validation - Stops CSRF attacks
✅ Proper HTTPS Enforcement - Encrypt data in transit
✅ Short-lived Authorization Codes - Minimize exposure windows
✅ Exact URI Matching - Prevent subdomain attacks without allowlists
The Bottom Line
Security isn't about creating the most restrictions – it's about creating the right restrictions. When your security measures make legitimate use cases harder while still allowing the most dangerous scenarios (hello, localhost!), you're not securing anything. You're just adding friction.
Real security comes from understanding attack vectors and implementing targeted defenses, not from blanket restrictions that look impressive but miss the point entirely.
What's your experience with OAuth implementations? Have you encountered similar examples of security theater? Share your thoughts in the comments below.